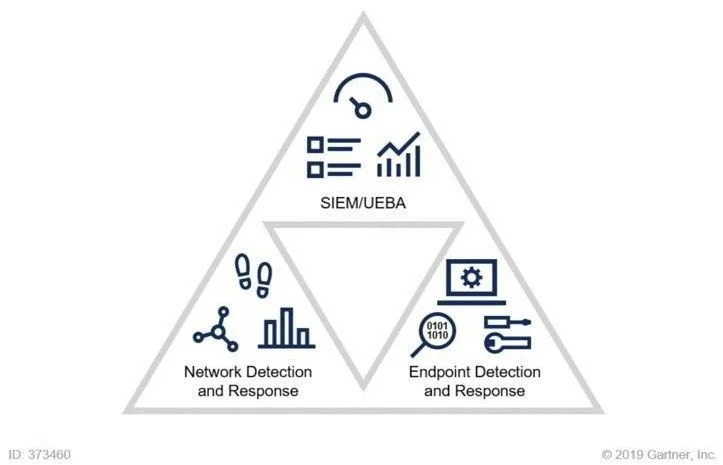
In today’s cyber landscape, staying ahead of threats isn’t just a goal—it’s a necessity. As cyber threats grow in sophistication and frequency, the need for robust security measures has never been more critical. Enter the SOC Visibility Triad: a fundamental framework that elevates the capabilities of Security Operations Centers (SOC) to new heights. By integrating Endpoint Detection and Response (EDR), Network Detection and Response (NDR), and Security Information and Event Management (SIEM), the SOC Visibility Triad provides a comprehensive approach to cybersecurity.
SOC Visibility Triad Overview
The SOC Visibility Triad is not just another buzzword in the cybersecurity world; it’s a strategic framework designed to provide unprecedented visibility into your organization’s security posture. At its core, the triad emphasizes the importance of endpoint, network, and log visibility, ensuring that no corner of your digital environment goes unmonitored.
Endpoint Visibility (EDR – Endpoint Detection and Response)
Endpoints are the gateways to your network and often the first targets of cyber attacks. Endpoint visibility through EDR is crucial because it allows for real-time monitoring and response to threats on individual devices. By keeping a vigilant eye on endpoints, organizations can detect and mitigate potential threats before they escalate.
Key Features of EDR
- Real-time Monitoring: EDR tools continuously monitor endpoint activities, providing instant data to detect anomalies and suspicious behavior. This real-time insight is essential for identifying and responding to threats as they occur.
- Advanced Threat Detection: Leveraging machine learning and behavioral analysis, EDR solutions can identify sophisticated threats that traditional antivirus solutions might miss. These technologies analyze patterns and behaviors to flag potential risks.
- Endpoint Profiling and Asset Management: Effective endpoint visibility also involves maintaining an up-to-date inventory of all devices connected to the network. Knowing what’s on your network is half the battle in securing it.
Network Visibility (NDR – Network Detection and Response)
Network visibility is about seeing the unseen within your data traffic. NDR solutions play a pivotal role in monitoring network traffic to identify malicious activities. By understanding normal traffic patterns, NDR tools can flag unusual behaviors indicative of a breach.
Key Features of NDR
- Real-time Traffic Analysis: NDR tools utilize advanced techniques to monitor and analyze data flow across the network continuously. This real-time analysis enables quick identification of anomalies.
- Deep Packet Inspection and Behavior Analysis: By inspecting the contents of data packets and analyzing network behavior, NDR solutions can detect malware and sophisticated cyber threats that might otherwise go unnoticed.
- Network Flow Monitoring: Tracking data movement across the network helps identify security gaps and understand how and where data is flowing, aiding in the prevention of data exfiltration and other malicious activities.
Log Visibility (SIEM – Security Information and Event Management)
Log data is the forensic goldmine of cybersecurity, offering detailed records of all activities within an IT environment. SIEM solutions centralize and analyze this log data to provide comprehensive security monitoring.
Key Features of SIEM
- Centralized Log Collection and Storage: SIEM platforms collect logs from various sources, creating a unified repository for easy access and analysis. This centralization is crucial for a holistic security view.
- Automated Log Analysis and Correlation: Automation in SIEM systems allows for the correlation of log data to detect patterns and potential threats. These systems can sift through massive amounts of data to identify risks quickly.
- Real-time Alerting: Prompt alerts are vital for swift incident response. SIEM solutions provide real-time notifications to ensure that security teams can act immediately upon detecting threats.
The Power of the SOC Visibility Triad
When EDR, NDR, and SIEM are integrated, they form a powerful defense mechanism that greatly enhances the efficacy of security operations. The combined visibility across endpoints, network traffic, and log data enables a more proactive and comprehensive approach to cybersecurity.
Examples of the Triad in Action
Consider a scenario where an unusual data transfer is detected by the NDR system. Simultaneously, the EDR tool identifies suspicious activity on an endpoint, and the SIEM correlates these events with historical data, confirming a potential breach. The triad’s integrated approach allows for immediate containment and investigation, significantly reducing the impact of the threat.
Conclusion
The SOC Visibility Triad is a game-changer in cybersecurity, providing the depth and breadth of visibility needed to stay ahead of evolving threats. By implementing EDR, NDR, and SIEM, organizations can achieve a robust security posture that not only detects but also prevents cyber incidents.
Ready to take your cybersecurity to the next level? Contact us today to learn how the SOC Visibility Triad can transform your security operations and keep your business safe.



